EVE - The Emulated Virtual Environment
For Network, Security and DevOps
Professionals
EVE - The Emulated Virtual Environment
For Network, Security and DevOps
Professionals
EVE - The Emulated Virtual Environment
For Network, Security and DevOps
Professionals
EVE - The Emulated Virtual Environment
For Network, Security and DevOps
Professionals
EVE - The Emulated Virtual Environment
For Network, Security and DevOps
Professionals
EVE-NG Professional Edition Latest Now: Release 5.0.1-144, 21 April, 2024

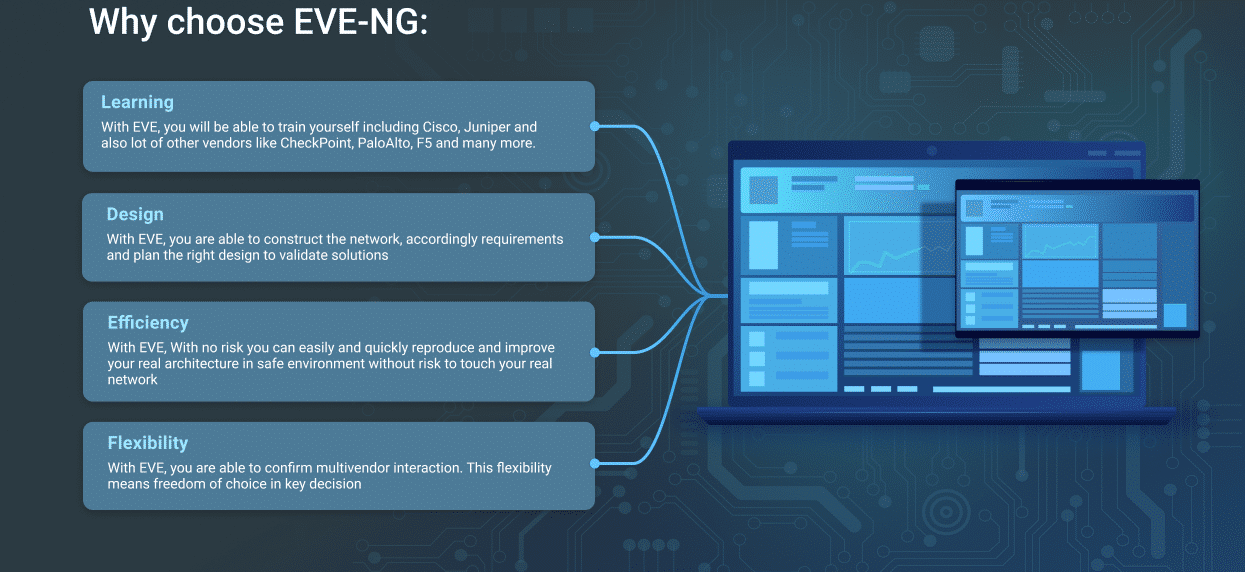
EVE-NG PRO platform is ready for today’s IT-world requirements. It allows enterprises, e-learning providers/centers, individuals and group collaborators to create virtual proof of concepts, solutions and training environments.
EVE-NG PRO is the first clientless multivendor network emulation software that empowers network and security professionals with huge opportunities in the networking world. Clientless management options will allow EVE-NG PRO to be as the best choice for Enterprise engineers without influence of corporate security policies as it can be run in a completely isolated environment.
| EVE-NG Professional/Learning Center Cookbook |
| EVE-NG PRO/LC Cookbook version 5.15 (03 APR, 2024)
Download link EVE PRO/LC Cookbook
Section updates in v 5.15
- Chapter 14.12 Cluster Offline upgrade
- Chapter 18, EVE Backup manager
|
Some Features:
EVE brings You the power You need to mastering your network within multivendor environment designing and testing.

- KVM HW accelaration
- Topology designer “click and play”
- Import/export configuration
- Labs xml file format
- Picture import and maps “click and play”
- Custom Kernel support for L2 protocols
- Memory optimization ( UKSM )
- CPU Watchdog
- Full HTML5 User Interface
- Ability to use without additionnals tools
- Multiusers
- Interaction with real network fully supported
- Simultaneous lab instances
- Derivated from Ubuntu LTS 20.04 server for long term support
|
EVE-NG-PRO Emulation Software
The brand new structure is created with many updated features and improvements.
- Dynamic console porting, no limits, fixing issues for multi user consoling, Telnet porting choose is random
- Hot links, interconnection running nodes, ports immediately response, shut no shut, Ethernet only
- 1024 nodes support per lab
- Docker containers support
- HTML desktop console to EVE management, clientless EVE management
- Closing feature of running lab placing it to running folder, option run more than one lab simultaneously
- Import/export configs for eve lab to/from local PC
- Multiuser support, Administrator role only
- EVE User account access time limitation
- NAT cloud, integrated NAT option with DHCP on the EVE
- Integrated Wireshark capture using docker, ethernet only
- Multi configurations for single lab
- Lab design features, links and objects
- Custom template for own node deployment
- Lab timer for self-training
- EVE Labs control management
- Information display of running labs and nodes per user. Admin control of processes
- Link quality bandwidth, delay, jitter and loss set feature
- EVE Cluster
- Google Cloud EVE PRO support
|
Upcoming features in EVE-NG PRO:
- Current version display and the newest available
- New lab design options
- Lab search option
- Live lab resource widget, CPU, RAM
- Lab timer, countdown improvement
|
|
![]()


